Google Chrome and Microsoft Edge supports the retrieval of the currently logged-in user's email. We leverage this API to obtain the email, generate a hash, and transmit it to our servers for user identification.
Prerequisites:
Ensure that you have both ADM and ADMX templates for Edge and Chrome browsers, available for download in the following zip files:
Setup:
- Utilizing GPO Templates: Install these templates in the same manner as browser templates, enabling you to modify client keys in the GPO editor.
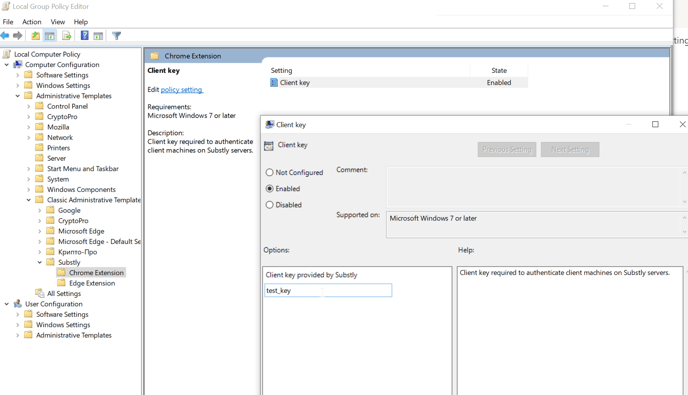
- Adding Your Client Key: Locate your unique key on the Substly Extension -> Settings tab.
Auto Registration trigger:
The extension attempts registration on every startup if:
- The user is not registered yet
- Client Key is specified
- Email is available (Note: It's possible that the user is not logged in to the browser or is using an account that doesn't provide email information)
Known Limitation for MS Edge:
For chrome.identity.getProfileUserInfo to function, the user must be signed into Microsoft Edge using a Microsoft account (MSA) or a Microsoft Entra ID account. If the user is signed in using an on-premises Microsoft Entra ID account, the API will return null for the email and ID values.
Quick demo
Troubleshooting
In Google Chrome, you can check the extension GPO configuration on the chrome://policy/ page: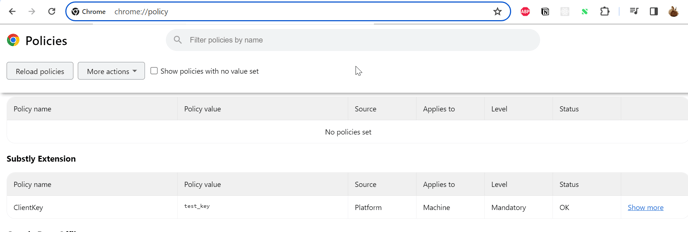
So you can test if Chrome is able to see the Client Key value. Unfortunately, for some reason, in Edge, you can't view the same information on the edge://policy/ page.
